Why Network Security Assessment is Critical for Your Business

A network security assessment is a systematic evaluation of your organization's IT infrastructure to identify vulnerabilities, security gaps, and potential threats before cybercriminals can exploit them.
Quick Answer - Network Security Assessment Essentials:
- Purpose: Identify vulnerabilities and security weaknesses in your network
- Types: Vulnerability assessments, penetration testing, compliance audits
- Frequency: At least annually, quarterly for high-risk environments
- Key Benefits: Prevent data breaches, ensure compliance, reduce costs
- Process: Planning → Scanning → Testing → Analysis → Reporting → Remediation
The numbers tell a stark story. Cyberattacks increased by 38% in 2022, with the average cost of a data breach reaching a record high of $4.35 million. According to cybersecurity experts, a zero-day vulnerability has an average lifespan of 348 days before vendors release a patch - plenty of time for attackers to cause serious damage.
Here's the reality: no business is too small to be targeted. Whether you're a healthcare provider handling patient data or a manufacturing company protecting trade secrets, cybercriminals are actively looking for ways into your network. The question isn't if you'll face a cyber threat, but when.
Network security assessments shift you from reactive to proactive security. Instead of waiting for an attack to reveal your weaknesses, these assessments help you find and fix vulnerabilities before they become expensive problems. Think of it as a health checkup for your IT infrastructure - identifying issues early when they're easier and cheaper to treat.
I'm Scott Crosby, and through my work at EnCompass and experience with IBM, I've seen how regular network security assessments can save businesses from costly breaches and downtime. My background in both business and computer science has shown me that the most successful companies treat cybersecurity as a strategic investment, not just an IT expense.

What is a Network Security Assessment and Why is it Crucial?

A network security assessment is a health checkup for your business's digital infrastructure. It's a comprehensive evaluation of your network's security posture, examining everything from firewalls to workstations to find vulnerabilities cybercriminals could exploit. This matters because your network is like a fortress protecting valuable assets. Over time, defenses weaken and new threats emerge. An assessment finds these weak spots before attackers do.
The benefits are significant:
- Protecting sensitive data: Assessments help ensure customer information, financial records, and proprietary data stay secure.
- Ensuring business continuity: By proactively fixing issues, assessments prevent devastating operational disruptions caused by cyberattacks.
- Reducing financial risk: With the average data breach costing $4.35 million, investing in security evaluations is a smart preventative measure.
- Strategic security planning: Instead of guessing, you get clear data on the greatest risks, allowing you to optimize your security budget and get maximum value from your spending.
The consequences of skipping regular assessments can be severe, including financial losses, legal liability, regulatory fines, and lasting reputational damage.
For businesses looking to strengthen their overall IT security posture, our comprehensive IT Support services provide ongoing protection and peace of mind.
Types of Network Security Assessments
Different security challenges require different approaches. We tailor our assessment methods based on your specific needs, industry requirements, and risk profile.
Vulnerability assessments serve as the foundation of network security evaluation. This is a detailed inventory of potential weak spots. We use scanning tools to identify known security flaws like missing patches, weak password policies, or outdated configurations. The process shows where vulnerabilities exist without exploiting them.
Penetration testing takes the evaluation a step further by simulating real-world cyberattacks. While a vulnerability assessment finds weak locks, penetration testing tries to pick them. This ethical hacking approach reveals how an attacker could chain vulnerabilities to gain deeper access.
Compliance assessments focus on meeting specific regulatory requirements that apply to your industry. Whether you need to comply with HIPAA, PCI DSS, or GDPR, these assessments verify that your security practices meet legal standards and help you avoid costly fines.
Configuration reviews examine the detailed security settings across all your network devices, servers, and workstations. Even advanced tools fail if misconfigured. We check everything from firewall rules to user permissions to ensure they follow industry standards.
Architecture reviews take a big-picture look at how your entire IT infrastructure fits together. We examine how systems communicate, where data flows, and whether the overall design creates unnecessary risks or blind spots.
For a more detailed exploration of one of these critical assessment types, you can read an overview of vulnerability assessments.
Black Box vs. White Box vs. Grey Box Testing
When we conduct penetration testing, the amount of information we have about your network beforehand determines our testing approach. Each method simulates different types of real-world attack scenarios.
| Testing Type | Tester Knowledge | Typical Targets | Primary Goals |
|---|---|---|---|
| Black Box | Zero internal knowledge (like a real attacker) | Externally facing applications, network perimeter, web applications | Simulate an external attacker, identify publicly exposed vulnerabilities, assess external defense mechanisms |
| White Box | Full internal knowledge (network diagrams, source code, credentials) | Internal systems, specific applications, code-level vulnerabilities, authenticated user access | Identify hidden vulnerabilities, assess internal controls, ensure secure coding practices, evaluate insider threat potential |
| Grey Box | Limited internal knowledge (e.g., user credentials, network segments) | Specific application functionalities, internal network segments, lateral movement paths | Simulate a semi-trusted insider or an attacker who has gained initial access, assess privilege escalation and lateral movement capabilities |
Black box testing mirrors how an external cybercriminal would approach your network—with no inside knowledge. This approach is excellent for understanding how well your perimeter defenses work against unknown attackers.
White box testing assumes the tester has comprehensive knowledge of your systems, similar to a malicious insider. This thorough approach often uncovers subtle vulnerabilities that other methods might miss.
Grey box testing strikes a middle ground, simulating scenarios where an attacker has gained limited access. This approach is valuable for understanding how far an intruder might get once they've breached your initial defenses.
The 6-Step Network Security Assessment Process
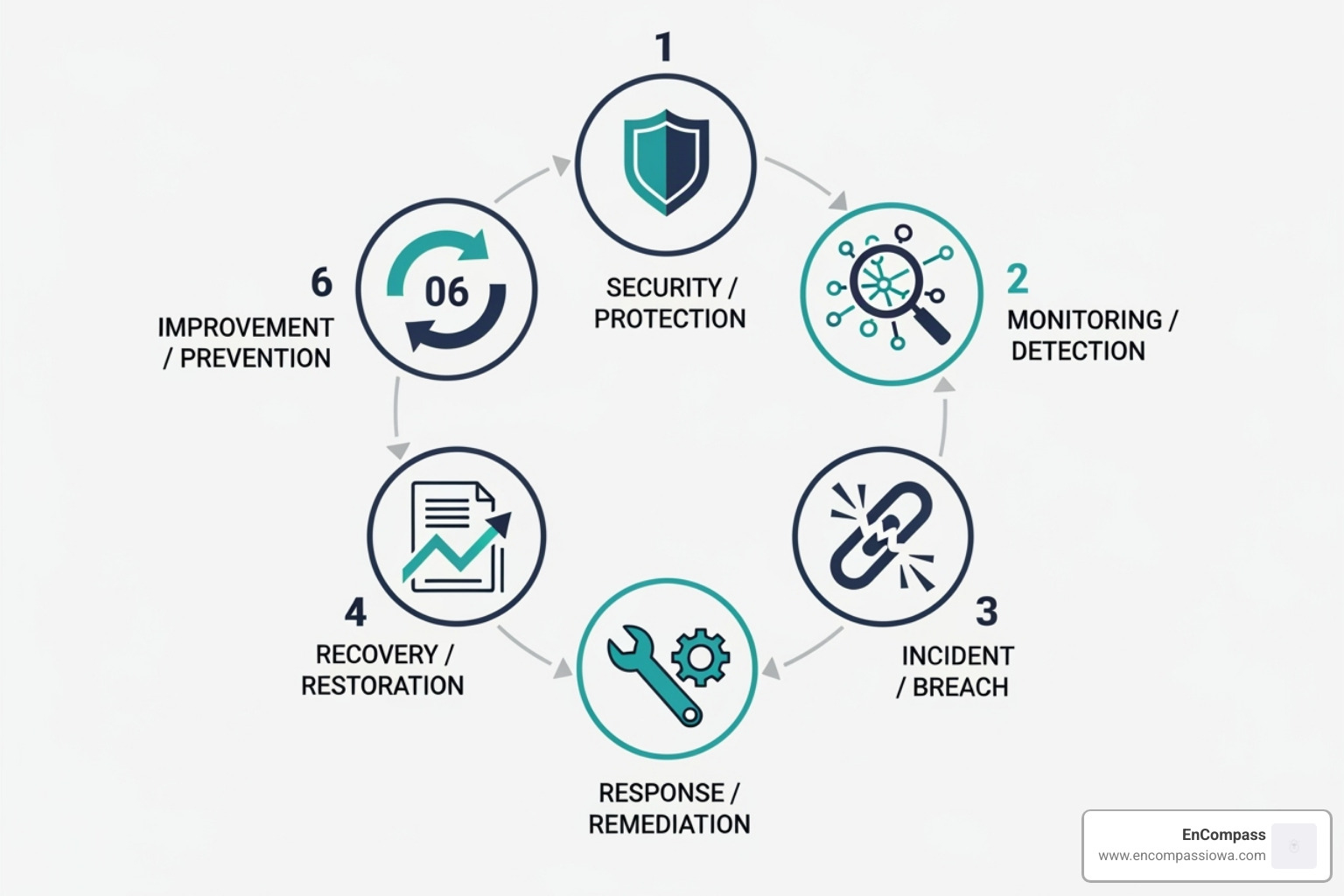
A network security assessment is like a home inspection for your digital infrastructure. Just as you'd check a house's foundation, you must regularly examine your network's health. Our approach is a proven, six-step methodology designed as a continuous, iterative cycle. This ensures we catch emerging vulnerabilities and keep your defenses strong over time, as cyber threats are constant.
Step 1 & 2: Planning, Scoping, and Findy
The foundation of an effective assessment is understanding what to protect and why. This initial planning involves:
- Defining objectives and scope: We determine your primary concerns, whether it's compliance, protecting sensitive data, or understanding your overall posture, to focus our efforts effectively.
- Assembling the team: We bring together key people from your organization, including IT, security, compliance officers, and department heads, to gain a comprehensive perspective.
- Asset inventory: We catalog all your digital assets—hardware, software, and data—to create a roadmap for the assessment.
- Reconnaissance: We gather publicly available information to see your network as an attacker would, helping us identify potential attack vectors.
Step 3 & 4: Scanning and Simulated Attacks
This phase involves active testing using both automated and manual techniques.
- Automated vulnerability scanning: We use specialized tools to systematically check your network for known vulnerabilities, such as missing patches, weak configurations, or unnecessary services.
- Penetration testing: We act as "ethical hackers" to exploit weaknesses in a controlled manner. This tests if your defenses hold up against real-world attack techniques without causing damage. The role of automation is critical for speed and scale, but it's most effective when combined with human expertise to validate findings and analyze complex attack scenarios.
For businesses looking for ongoing protection beyond assessments, our Managed IT Services provide continuous monitoring and threat detection.
Step 5 & 6: Analysis, Reporting, and Remediation
The final steps focus on understanding the findings and taking action.
- Prioritizing risks: We use frameworks like the Common Vulnerability Scoring System (CVSS) combined with your business context to rate the severity of each finding.
- Creating a detailed report: We provide a report with an executive summary for leadership and detailed technical findings for your IT team. Our reports include actionable recommendations that are practical and realistic for your organization.
- Implementing fixes: We work with your team to apply the necessary remedies, such as patching software, updating configurations, or strengthening access controls.
- Continuous monitoring: Security is an ongoing process. Regular monitoring ensures your defenses evolve to meet new threats as your network changes.
Key Benefits of Performing Regular Assessments
Regular network security assessments are a strategic investment that acts as your business's early warning system. Key benefits include:
- Proactive threat prevention: You find and fix weak spots before cybercriminals can exploit them, dramatically reducing your risk of a data breach.
- Strengthened security posture: Each assessment builds on the last, creating a more resilient and layered defense system over time.
- Improved incident response plans: Understanding your vulnerabilities allows you to prepare more effective and targeted response strategies.
- Competitive advantage: Demonstrating a commitment to security builds trust with customers and partners who want to work with businesses that protect their data.
- Support for distributed work environments: With the rise of remote work, your security perimeter has expanded. Assessments help ensure these remote access points remain secure. For more insights on protecting your remote workforce, explore our Remote Work security solutions.
Achieve and Maintain Regulatory Compliance
For many businesses, assessments are legally required. Smart business owners view compliance not as a burden, but as a framework for stronger security. Assessments help you meet legal and industry standards like HIPAA, PCI DSS, and GDPR, which all mandate regular security evaluations. Your assessment reports provide concrete evidence for auditors, demonstrating due diligence and a proactive security posture. This helps in avoiding fines and penalties, which can be staggering.
A comprehensive network security assessment also directly impacts your Identity and Access Management systems, ensuring that only authorized personnel can access sensitive data and systems.
Reduce Costs and Protect Your Reputation
Regular assessments are one of the smartest financial investments for your business.
- Avoiding data breach costs: With average breach costs exceeding $4.35 million, preventing a single incident provides a massive return on investment.
- Preventing operational downtime: Cyberattacks can halt operations. Assessments identify and fix issues that could lead to costly interruptions.
- Building trust and protecting your brand: A strong security posture builds trust with customers and partners. It becomes part of your brand identity, showing you are a responsible steward of data.
It is far less expensive to maintain good security through regular assessments than to rebuild trust and operations after a breach. Regular network security assessments aren't just about preventing problems – they're about positioning your business for sustainable growth and success.
Frequently Asked Questions about Network Security Assessment
Business owners often ask about network security assessments, especially when considering one for the first time or after hearing about a local cyberattack. Here are the most common questions we hear and our straight answers.
How often should a network security assessment be conducted?
The ideal frequency depends on your specific situation.
- For most businesses, at least once a year is a solid baseline to stay ahead of new threats.
- For high-risk industries like healthcare or finance, quarterly assessments are recommended due to higher stakes and regulatory requirements.
- An assessment should also be run after any significant network changes, such as adding new software, upgrading servers, or moving to the cloud, as these can introduce new vulnerabilities.
The gold standard is continuous monitoring combined with periodic full assessments to provide real-time protection between deeper evaluations.
Who should be involved in the assessment process?
A successful assessment is a business-wide project, not just an IT task. Key participants should include:
- IT and security teams: They have the technical knowledge of your systems and will implement fixes.
- Senior management: Their buy-in is essential for budget and strategic alignment, as cybersecurity decisions affect the entire business.
- Compliance officers: In regulated industries, they ensure all legal requirements are met and documented for audits.
- Department heads: They provide context on data sensitivity and business impact, helping to prioritize efforts.
- External experts: Partnering with specialists like our Managed Services team provides an outside perspective and specialized knowledge without the overhead of hiring full-time staff.
What are common vulnerabilities assessments uncover?
We consistently find the same common, preventable vulnerabilities, which usually stem from overlooked security hygiene. The most frequent issues include:
- Outdated software and unpatched systems: Failing to apply security patches leaves known vulnerabilities open for exploitation.
- Weak passwords: Default, simple, or reused passwords are an easy entry point for attackers.
- Misconfigured firewalls and unnecessary services: Open ports or outdated firewall rules create unnecessary risks, as do services running on servers that aren't needed.
- Missing or weak data encryption: Sensitive data stored or transmitted without encryption is a major risk.
- Web application flaws: Issues like SQL injection or cross-site scripting (XSS) can give attackers direct access to databases.
- Susceptibility to phishing attacks: Even with strong technical defenses, an employee can be tricked into giving away credentials, bypassing security measures.
The good news is that once identified, most of these vulnerabilities are straightforward to fix. The key is finding them first.
Conclusion: Fortify Your Defenses with Proactive Assessments
The digital landscape has fundamentally changed how we think about business security. Network security assessments aren't just another item on your IT checklist – they're the cornerstone of a modern cybersecurity strategy that can make or break your business.
Think about it this way: you wouldn't drive a car without regular maintenance, and you shouldn't run a business without regularly checking your digital defenses. The shift from reactive to proactive security is what separates businesses that thrive from those that merely survive cyber threats.
When you conduct regular network security assessments, you're essentially giving yourself a crystal ball. You can see potential problems before they become expensive disasters. You can fix vulnerabilities before attackers find them. You can sleep better at night knowing your business is protected.
The benefits we've discussed – from preventing costly data breaches to maintaining regulatory compliance – all stem from this proactive approach. Whether you're protecting patient records, customer payment information, or proprietary business data, regular assessments help you stay one step ahead of cybercriminals.
At EnCompass, we've seen how businesses in the Cedar Rapids Corridor transform their security posture through strategic assessments. We understand that every business is unique, with its own challenges and requirements. That's why we focus on providing cost-effective, reliable IT solutions that don't just meet your current needs but grow with your business.
Our approach combines technical expertise with a deep understanding of local business needs. We don't just identify problems – we work with you to implement practical solutions that strengthen your defenses without breaking your budget. It's about building a partnership where your success is our success.
The threat landscape will continue to evolve, but with regular network security assessments as part of your cybersecurity strategy, you'll be ready for whatever comes next. Your business deserves protection that works as hard as you do.
Ready to take the next step? To understand your network's vulnerabilities and build stronger defenses, explore our Network Security Assessment services. Let's work together to secure your digital future and keep your business moving forward with confidence.


