Why Network Vulnerability Scanning is Your Business's Digital Health Check
Network vulnerability scanning is the process of automatically inspecting your network infrastructure, devices, and systems to identify security weaknesses that hackers could exploit. Think of it as a comprehensive health check for your digital environment.
What Network Vulnerability Scanning Reveals:
- Unpatched software and outdated firmware on servers, routers, and workstations
- Misconfigured devices with weak security settings or default passwords
- Open ports and unnecessary services that create attack entry points
- Compliance gaps that could result in regulatory penalties
- Risk prioritization based on severity and potential business impact
With 95% of businesses now focusing on IT readiness to combat evolving cybersecurity threats, regular vulnerability scanning has become essential for maintaining security and compliance. Most compliance standards like PCI DSS and ISO27001 require vulnerability scanning at least quarterly, with many organizations scanning monthly or even weekly.
The process works by sending automated probes across your network to catalog all connected devices, then testing each one for known security flaws. Modern scanners check against comprehensive vulnerability databases and provide detailed reports with remediation guidance.
The reality is stark: unpatched software and firmware remain leading causes of major data breaches, as attackers constantly monitor public vulnerability disclosures looking for targets that fail to patch quickly.
I'm Scott Crosby, and through my work in technology at EnCompass - where we've helped establish award-winning managed IT services - I've seen how effective network vulnerability scanning programs protect businesses from costly security incidents. My experience attending numerous technology events and contributing to client security initiatives has shown me that vulnerability management doesn't have to be overwhelming when approached systematically.
What is Network Vulnerability Scanning and Why It Matters
Think of network vulnerability scanning as having a security expert walk through your digital building, checking every door, window, and lock to find weak spots before burglars do. This automated process thoroughly examines your network infrastructure, identifying security gaps that cybercriminals could exploit to break into your systems.
Unlike a simple network scan that just maps what's connected to your network, network vulnerability scanning goes deeper. It's specifically hunting for security flaws - those open doors and broken locks that could spell trouble for your business. The scanner checks every device, from your main servers down to that forgotten printer in the corner office, looking for unpatched software, weak passwords, and misconfigurations that hackers love to find.
For businesses in the Cedar Rapids Corridor, this isn't just about being cautious - it's about survival in today's digital landscape. Networks have become the second most vulnerable breach point after applications, making proactive security assessment absolutely critical. When you consider that a single overlooked vulnerability can cost your business everything from customer trust to regulatory fines, the value of regular scanning becomes crystal clear.
Our comprehensive network security services help businesses understand exactly where their vulnerabilities lie and how to fix them effectively.
How Network Vulnerability Scanning Differs from Other Security Assessments
Understanding what makes network vulnerability scanning unique will help you make better security decisions.
- Network scanning simply maps devices and services. Network vulnerability scanning goes further by testing those devices for exploitable weaknesses.
- Web application scanning targets websites for issues like SQL injection, while database scanning checks database configurations. Network vulnerability scanning provides a broader view, covering the entire infrastructure—firewalls, routers, and servers.
- Penetration testing is different; it actively tries to exploit found vulnerabilities to confirm their impact. Vulnerability scanning finds the open doors, while penetration testing walks through them. Scanning provides the foundational security assessment.
The Critical Role in Modern Cybersecurity
Network vulnerability scanning has evolved from a nice-to-have security practice into an absolute business necessity. Here's why it matters so much for your organization's survival and success.
- Preventing Data Breaches: Unpatched systems and misconfigured devices are easy targets. Attackers race to exploit newly disclosed flaws before businesses can apply patches. A single vulnerability can lead to a full network compromise and theft of valuable data.
- Meeting Compliance Requirements: Standards like PCI DSS, ISO27001, and NIST mandate regular vulnerability scans. Non-compliance can lead to heavy fines, lost certifications, and damaged business relationships.
- Ensuring Business Continuity: A cyberattack can halt operations for days or weeks. Proactively finding and fixing vulnerabilities protects your uptime, allowing your business to focus on growth instead of crisis management.
Types and Methods of Network Vulnerability Scanning
Just as a doctor might use different tools for different parts of a health check, there are various types and methods of network vulnerability scanning, each offering a unique perspective on your security posture.
Authenticated vs Unauthenticated Scanning
The primary distinction in scanning methods often comes down to access:
- Unauthenticated Scanning: Performed without login credentials, this scan mimics an external attacker's view. It's great for finding surface-level weaknesses like open ports and exposed services but may miss deeper configuration issues.
- Authenticated Scanning: This scan uses valid credentials to log into systems, enabling a deep inspection of configurations, patch levels, and software. It's like an internal audit, uncovering flaws not visible from the outside, such as misconfigurations, weak passwords, and unpatched software.
Internal vs External Network Vulnerability Scanning
The location from which a scan is performed also defines its type:
- External Network Vulnerability Scanning: Conducted from the internet, these scans target your public-facing assets like web servers, firewalls, and VPNs. They reveal what an outside attacker can see and potentially exploit.
- Internal Network Vulnerability Scanning: Performed from within your network, these scans simulate an insider threat or an attacker who has already breached the perimeter. They are vital for finding weaknesses that could allow an attacker to move laterally across your network. We often use secure VPN agents to assess hosts within your internal network. For more on continuous monitoring, see our guide on effective network monitoring techniques.
Cloud and Container Vulnerability Scanning
As businesses adopt modern infrastructure, scanning must also evolve:
- Cloud Vulnerability Scanning: This focuses on identifying misconfigurations in cloud environments (AWS, Azure, etc.), such as improper security group rules or storage permissions that could expose data.
- Container Vulnerability Scanning: This involves assessing the security of container images and runtime environments (like Docker). Integrating this into DevOps pipelines helps secure applications before they are deployed.
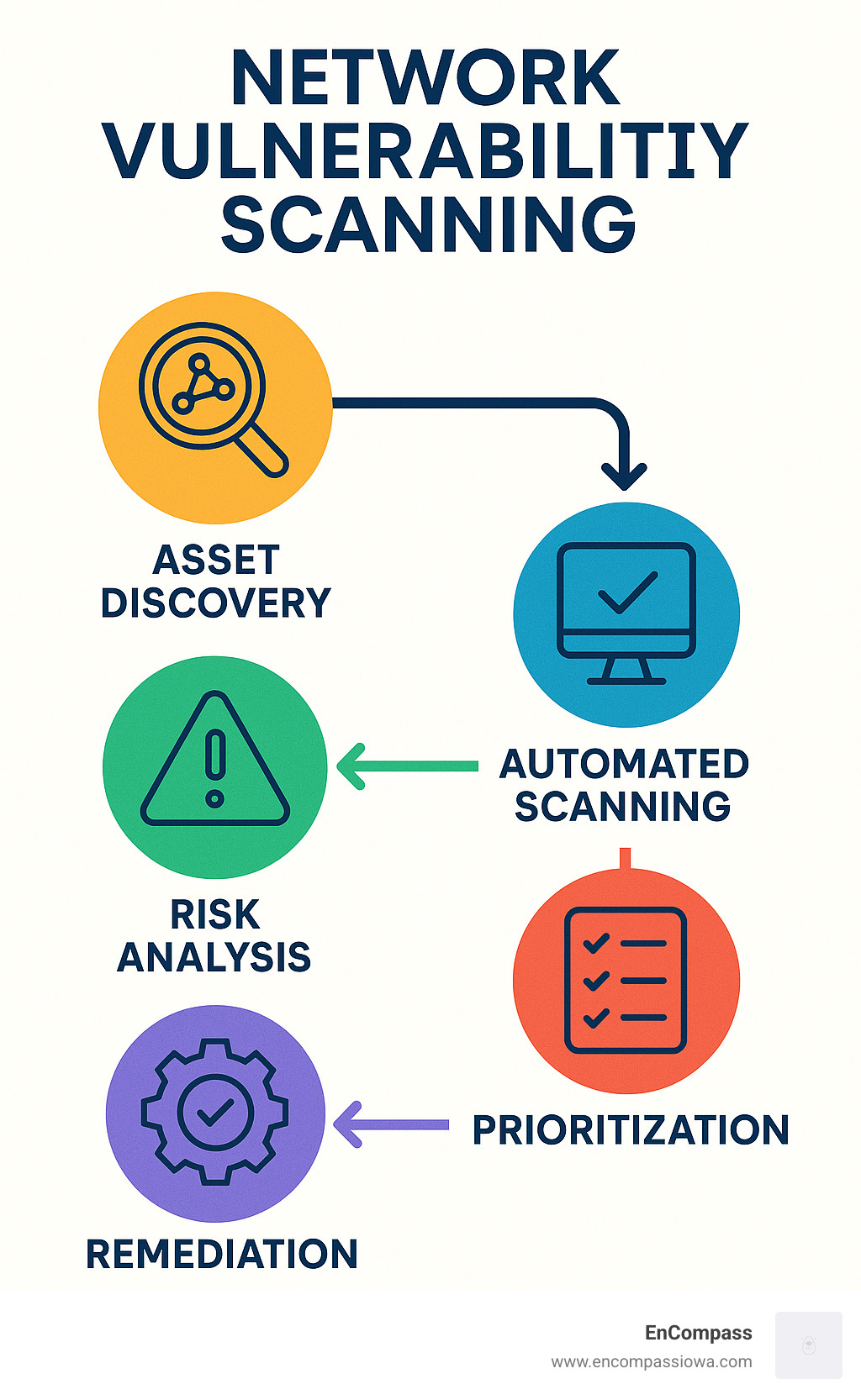
The Network Vulnerability Scanning Process Step-by-Step
Understanding how network vulnerability scanning works is key to implementing it effectively. The process is a methodical approach to creating a complete picture of your network's security health.

Asset Findy and Inventory Management
You can't protect what you don't know you have. The first step is creating a complete inventory of all network assets. This involves:
- Network Mapping: Identifying every device on your network, from servers and workstations to printers and IoT devices.
- Device Identification: Determining the operating system and type of each device to tailor security checks.
- Service Enumeration: Using tools like Network findy tools to find open ports and running services, which are potential entry points for attackers.
Maintaining a dynamic inventory is crucial, as networks constantly change. This continuous process ensures no device is left unsecured.
Scan Configuration and Execution
With a clear inventory, the scanning phase begins. This requires technical expertise to ensure scans are both effective and non-disruptive.
We use scan templates with predefined configurations for different devices and environments. Scheduling is planned carefully to minimize impact on business operations, whether scans are quarterly for compliance or more frequent. During execution, the scanner sends automated probes that can generate significant network traffic. While the scanning is thorough, it's important that your network can handle the additional load. An IPS protection system can help monitor scanning activity and potential threats.
Analysis and Risk Prioritization
Scan results can be overwhelming, but a methodical analysis turns raw data into an actionable plan.
CVSS scoring provides a standard measure of severity, but we go further by considering exploit availability—whether active attack code exists. Business impact is also critical; a vulnerability on a core database is more urgent than one on a test system. We cross-reference findings with vulnerability databases like CVE to understand the full scope and develop realistic remediation timelines. The result is a prioritized action plan that focuses on the most significant risks to your business.
Common Network Vulnerabilities and Detection Strategies
Network vulnerability scanning is about finding the common weaknesses that cybercriminals exploit. Most successful attacks don't rely on sophisticated hacking but on common oversights that are easy to find and fix with proactive scanning.

Critical Infrastructure Vulnerabilities
Your core infrastructure—routers, switches, firewalls, and servers—can hide critical security gaps.
- Unpatched Software and Firmware: This is the biggest threat. Attackers use automated tools to find systems with known, unpatched vulnerabilities. All network devices need regular updates. For more on this, see our article on protecting your business from top software threats.
- Misconfigured Network Devices: Default credentials (like "admin/admin"), unsecured wireless networks, and improperly configured IoT devices are easy targets for attackers.
- Open Ports and Unnecessary Services: These are like open doors into your network. Vulnerability scanning identifies and helps close unnecessary entry points created by overly permissive firewall rules or services.
Application and Service Vulnerabilities
Beyond infrastructure, the applications running on your network present unique risks.
- Weak Authentication Systems: This includes easily guessable passwords, unchanged default credentials, and missing multi-factor authentication on critical systems.
- Web Services Vulnerabilities: Issues like SQL injection can allow attackers to manipulate databases, while cross-site scripting can hijack user sessions. Internal web applications also need scanning, as they are prime targets once an attacker is inside the network.
- Remote Access Vulnerabilities: Services like RDP and SSH are essential but are favorite targets. An improperly secured remote connection can give an attacker complete control over a system.
- Database System Vulnerabilities: Unpatched database software or weak access controls can expose your most sensitive data, from customer records to financial information.
Regular network vulnerability scanning excels at detecting all these issues before they become headlines, turning potential disasters into routine maintenance.
Best Practices for Effective Network Vulnerability Management
A successful network vulnerability scanning program requires ongoing attention and a systematic approach. With solid practices, vulnerability management becomes a well-oiled machine that protects your business.

Establishing Scan Frequency and Scheduling
How often should you scan? The answer depends on your business, but some guidelines apply to most organizations.
- Baseline Frequency: Quarterly scanning is the minimum for most businesses and is required by compliance standards like PCI DSS and ISO27001.
- Higher Frequency: For businesses handling sensitive data, monthly or even weekly scans are recommended to reduce the window of opportunity for attackers.
- Event-Driven Scans: Scan after major infrastructure changes, such as adding new servers, and after patch deployment cycles to verify that fixes were successful. This proactive approach is key, as explained in our article on reasons network security should be a top priority for your business.
Integration with Patch Management
Finding vulnerabilities is only half the battle; fixing them is what provides protection. Your scanning program must integrate with your patch management process.
- Risk-Based Prioritization: Use scan results to focus on critical issues first, especially those with publicly available exploits.
- Timely Remediation: Aim to fix high-severity vulnerabilities within one to two weeks. If you can't patch immediately, it's crucial to have a plan to mitigate the risk. Forbes offers guidance on what to do if you can't patch a software vulnerability.
- Verification: After applying patches, run another scan to confirm the vulnerabilities are gone.
Building a Vulnerability Management Program
Network vulnerability scanning is most effective as part of a broader program.
- Policies and Procedures: Document how vulnerabilities are identified, who is responsible, and the required remediation timelines.
- Roles and Responsibilities: Clearly define who owns scanning, analysis, and remediation to ensure a fast response.
- Continuous Monitoring: Go beyond scheduled scans to watch for new devices, configuration changes, and emerging threats.
- Training and Awareness: The human element is critical. Train your team to recognize and respond to security issues. Our guide on how to protect your company with cybersecurity awareness offers practical strategies.
- Metrics and Reporting: Track metrics like the number of critical vulnerabilities and time-to-remediate to measure success and demonstrate value.
Frequently Asked Questions about Network Vulnerability Scanning
When we talk with businesses throughout the Cedar Rapids Corridor about network vulnerability scanning, certain questions come up again and again. Here are answers to some of the most common ones.
How often should organizations perform network vulnerability scans?
The frequency depends on your risk profile and compliance needs. Quarterly scans are the recommended minimum, often required by standards like PCI DSS and ISO27001. However, businesses handling sensitive data should consider monthly or even weekly scans. It's also critical to scan after significant events, such as major software deployments, infrastructure changes, or after applying security patches, to ensure no new vulnerabilities were introduced.
What are the main challenges and limitations of network vulnerability scanning?
Scanning isn't a silver bullet and has some challenges:
- Information Overload: Scanners can produce a high volume of findings, making prioritization difficult without expert analysis.
- False Positives: Scans may incorrectly flag non-vulnerabilities, requiring manual verification to filter out the noise.
- Resource Impact: Scanning consumes network bandwidth and can impact system performance. Scans should be scheduled during maintenance windows to minimize disruption.
- Legacy Systems: Older systems may be incompatible with modern scanners or too risky to scan or patch, requiring alternative security controls.
How can organizations measure the effectiveness of their scanning efforts?
You can measure the success of your scanning program with several key metrics:
- Vulnerability Trends: Track the number of critical and high-severity vulnerabilities over time. A downward trend indicates an improving security posture.
- Mean Time to Remediate (MTTR): Measure the average time it takes your team to fix vulnerabilities. A decreasing MTTR shows improved efficiency.
- Scan Coverage: Ensure you are scanning all of your critical assets. Gaps in coverage are significant risks.
- Compliance Audits: Successfully passing audits is a clear indicator that your program is effective.
We help our clients generate comprehensive reports on these metrics to demonstrate the value of their cybersecurity investments to stakeholders.
Conclusion
Think of network vulnerability scanning as your business's early warning system – the digital equivalent of a smoke detector that never sleeps. In today's world where cyber threats evolve faster than most of us can keep up with our morning coffee, this isn't just another IT task to check off your list. It's become as essential as locking your office doors at night.
The beauty of vulnerability scanning lies in its proactive nature. Instead of waiting for something bad to happen and then scrambling to fix it, you're actively hunting down problems before they become disasters. It's like having a security guard who knows every potential weakness in your building and checks them regularly.
Throughout this guide, we've explored how network vulnerability scanning works as part of a larger security strategy. From understanding the different types of scans to building effective remediation workflows, the process doesn't have to feel overwhelming. When you break it down into manageable steps – asset findy, scanning, analysis, and fixing – it becomes a straightforward routine that protects everything you've worked to build.
The continuous cycle of scanning, analyzing, and fixing creates a security posture that gets stronger over time. Each scan teaches you more about your network, each remediation makes you more resilient, and each verification scan confirms you're moving in the right direction.
For businesses in the Cedar Rapids Corridor, maintaining this level of security vigilance means you can focus on what really matters – serving your customers and growing your business. You don't have to lie awake at night wondering if your network is secure or if you'll pass your next compliance audit.
At EnCompass, we've seen how the right approach to network vulnerability scanning transforms security from a source of stress into a competitive advantage. When your systems are secure and compliant, you can pursue opportunities with confidence, knowing your digital foundation is solid.
Ready to turn vulnerability management from a headache into peace of mind? Our comprehensive network security assessment services are designed to fit your business needs and budget, giving you the security you need without the complexity you don't want.


