Why Data Security Solutions Are Critical for Your Business Survival

Data security solutions are comprehensive tools and strategies designed to protect your organization's sensitive information from cyber threats, unauthorized access, and data breaches. These solutions include encryption, access controls, monitoring systems, and backup technologies that work together to create multiple layers of protection around your valuable business data.
Key types of data security solutions include:
- Encryption tools - Protect data at rest and in transit
- Identity and Access Management (IAM) - Control who can access what data
- Data Loss Prevention (DLP) - Monitor and prevent unauthorized data sharing
- Backup and recovery systems - Ensure business continuity after incidents
- Network security tools - Firewalls, antivirus, and intrusion detection
- Cloud security platforms - Protect data in hybrid and multi-cloud environments
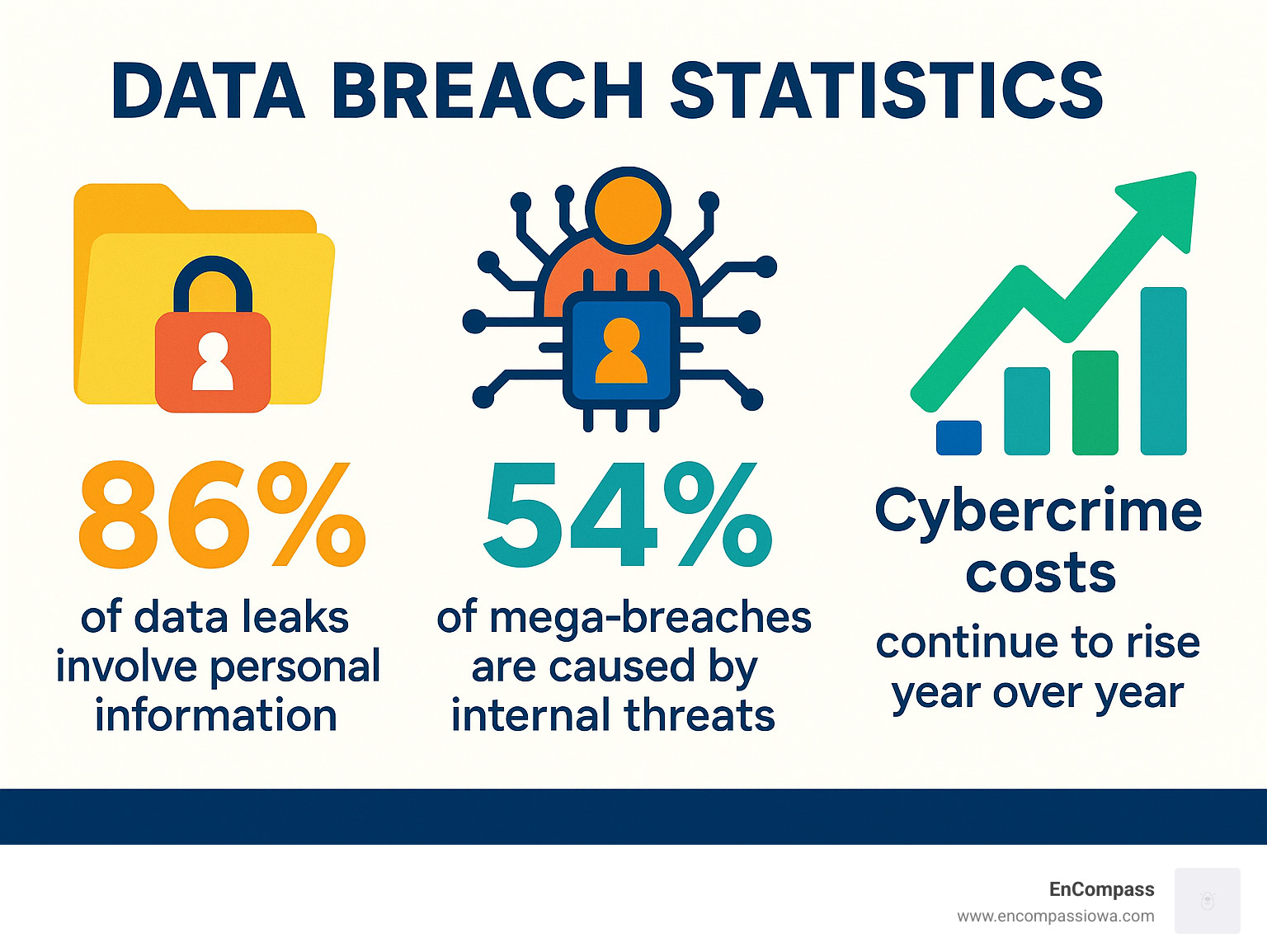
The numbers paint a stark picture of today's threat landscape. Research shows that 86% of data leaks involve personal information, while 54% of major breaches are caused by internal threats. With cybercrime reaching all-time highs and attacks becoming more sophisticated each year, no business—regardless of size—can afford to operate without robust data protection.
Your data isn't just files on a server. It's your customer information, financial records, intellectual property, and the foundation of your business operations. When that data is compromised, the consequences extend far beyond immediate financial losses to include damaged reputation, regulatory penalties, and potentially catastrophic business disruption.
Understanding Today's Data Security Challenges and Threats
Picture this: your business data is like water flowing through an increasingly complex network of pipes, valves, and containers. Some pipes run through your office, others stretch into the cloud, and a few connect to partner systems you barely control. Now imagine trying to keep every drop secure while new leaks spring up daily. That's the reality of modern data security solutions.
Complex IT environments have become the norm rather than the exception. Your data doesn't sit politely in one location anymore. Instead, it's scattered across hybrid cloud infrastructure, bouncing between on-premises data centers, public cloud platforms, and countless software applications. This data sprawl across platforms creates a security nightmare where protecting information feels like playing whack-a-mole.
Each new system adds another potential entry point for attackers. When your customer database lives in one cloud, your email runs on another platform, and your financial records sit on local servers, maintaining consistent security becomes incredibly challenging.
The evolving threat landscape isn't making things easier. Cybercriminals have essentially gone high-tech, using AI-powered attacks that can adapt and learn from your defenses in real-time. These aren't the simple viruses of yesterday—today's threats include sophisticated ransomware that can encrypt your entire business in minutes, deepfake technology that can fool even careful employees, and social engineering attacks that would make a con artist jealous.
What makes this even scarier is that insider threats remain one of the biggest risks. 54% of major breaches are caused by internal threats. This could be a disgruntled employee, someone who accidentally clicks the wrong link, or even a well-meaning staff member who doesn't realize they're putting data at risk.
Adding fuel to this fire is the growing pressure from regulations like GDPR, HIPAA, and CCPA. These aren't just guidelines—they're legal requirements with teeth. GDPR alone can fine businesses up to 4% of their global revenue for violations. These regulations demand that you know exactly what data you have, where it lives, who can access it, and how it's protected.
The challenge isn't just implementing data security solutions—it's doing so in a way that doesn't bring your business to a grinding halt. You need protection that's robust enough to stop sophisticated attacks but flexible enough to let your team work efficiently across all these complex systems.
The Blueprint for a Resilient Data Security Strategy
Think of building a resilient data security strategy like constructing a fortress around your most precious treasures. You wouldn't just put up one wall and call it good—you'd create multiple layers of defense, each designed to stop different types of threats. That's exactly how we approach data security solutions: through three interconnected pillars that work together to create an impenetrable shield around your business information.
Data Findy, Classification, and Governance
Here's a truth that might surprise you: most businesses have no idea what data they actually have or where it lives. It's like trying to guard a treasure chest when you don't know what's inside or where all the copies are hidden. This is why data findy and classification form the foundation of any effective security strategy.
Automated data classification tools are game-changers in this space. These smart systems can scan through your entire digital environment and accurately identify sensitive information like Personally Identifiable Information (PII), payment card data, and protected health information. The best part? Advanced platforms can achieve over 95% classification accuracy, which means they're incredibly reliable at spotting risky data movements and potential compliance violations.
Once we know what data you have, we implement strong data governance principles. This includes managing your data throughout its entire lifecycle—from the moment it's created until it's securely deleted. We also focus heavily on data minimization, which is a fancy way of saying "only keep what you actually need." The less sensitive data you store, the smaller your target becomes for cybercriminals.
Fortifying Access with Modern Controls
Even perfectly classified data becomes vulnerable the moment the wrong person gets their hands on it. That's why controlling access is absolutely critical to your data security solutions strategy.
We build everything around a Zero Trust architecture, which operates on a simple but powerful principle: "never trust, always verify." It doesn't matter if someone is the CEO calling from the office or a contractor working remotely—every single access request gets authenticated and authorized. No exceptions, no shortcuts.
At the heart of Zero Trust is the principle of least privilege. This means giving people only the minimum access they need to do their jobs effectively. Think of it like giving someone the key to one specific room instead of a master key to the entire building. If an account gets compromised, the damage stays contained.
Multi-factor authentication (MFA) adds crucial layers beyond just passwords. Instead of relying on something that can be guessed or stolen, MFA requires a second form of verification—maybe a code from your phone or a biometric scan. Even better, we're seeing a strong shift toward passwordless solutions that eliminate the weakest link in security: the password itself. These methods use biometrics or specialized keys that are incredibly resistant to phishing attacks.
Identity and Access Management (IAM) platforms tie all these controls together beautifully. They manage user identities and access rights across your entire environment, whether that's cloud, hybrid, or on-premises systems. This centralized approach streamlines everything from onboarding new employees to ensuring departing staff lose access immediately.
The Crucial Role of Encryption
If your data is the treasure, then encryption is the uncrackable vault protecting it. Some security experts argue that a business that only encrypts its data is more secure than one that does everything else—that's how foundational encryption is to modern data security solutions.
Encryption protects your data in two critical states: when it's sitting still (data-at-rest) and when it's moving around (data-in-motion). For stored data, we implement strong encryption for all sensitive information, especially PII. Many hardware solutions use AES 256-bit hardware encryption, which meets the highest compliance standards and includes tamper-resistant designs that can even perform real-time anti-malware scanning.
For data traveling across networks, network encryptors secure information as it moves between locations or from your office to the cloud. These systems support high network speeds, so you get bulletproof security without sacrificing performance.
The real magic happens with centralized key management and Hardware Security Modules (HSMs). These systems generate, store, and manage encryption keys securely, ensuring that only authorized people can decrypt your data. HSMs act as hardware-based trust anchors and are so reliable they secure an estimated 80% of global point-of-sale transactions.
We're even seeing exciting developments like homomorphic encryption, which allows data to be processed and searched while it's still encrypted. This means your information never has to be exposed, even when it's being used—adding yet another layer of protection to your digital fortress.
A Comparative Look at Modern Data Security Solutions
The world of data security solutions can feel overwhelming at first glance. Picture it like building a house—you need a solid foundation before you can add the fancy smart home features. The same principle applies to protecting your business data. Let's walk through the different layers, from the basics every organization needs to the advanced tools that offer cutting-edge protection.
Foundational Security Layers
These are your digital fortress's basic building blocks. Without them, even the most advanced security tools will crumble like a house of cards.
Endpoint protection is where it all starts. Every laptop, desktop, and mobile phone connected to your network is a potential doorway for attackers. Modern endpoint solutions do more than just detect threats—they monitor device behavior, patch vulnerabilities automatically, and even include application self-healing capabilities. Think of them as having a security guard at every possible entrance to your building.
Network firewalls act like the gates and walls around your digital property. They examine every piece of data trying to enter or leave your network, following rules you've set up. The key is keeping these rules updated as new threats emerge—yesterday's firewall settings might not catch today's sophisticated attacks.
Antivirus and antimalware tools are your basic immune system. While they're absolutely necessary, modern cyber threats are getting sneaky enough to slip past traditional detection methods. That's why they work best as part of a larger security ecosystem rather than standing alone.
Here's something many businesses overlook: secure portable storage. Those innocent-looking USB drives can be major security risks. Modern encrypted USB solutions use AES 256-bit hardware encryption with centralized management platforms that let you control thousands of devices remotely. It's no coincidence that over 70% of Fortune 100 companies trust these solutions for their portable data needs.
Vulnerability management keeps your systems healthy by continuously finding and fixing security weaknesses. The best solutions automate this process, minimizing downtime from faulty updates and restoring your systems in hours rather than days.
Advanced Data-Centric Security Solutions
Once your foundation is solid, these advanced solutions focus directly on your data and how it behaves. They're like having a personal bodyguard for your most valuable information.
Data Loss Prevention (DLP) solutions are your data's watchful guardians. They monitor every email, cloud upload, and USB transfer to make sure sensitive information doesn't slip out the back door. The magic happens when DLP works with accurate data classification—automatically tagged sensitive data gets the protection it deserves without slowing down your team's productivity.
Data Security Posture Management (DSPM) is the new kid on the block, but it's growing fast for good reason. These platforms act like security detectives, finding and classifying sensitive data across every corner of your IT environment. They answer critical questions like "Who has access to our customer data?" and "Is our financial information properly protected?" Gartner predicts that by 2026, over 20% of organizations will use DSPM technology—and for good reason. Early breach warnings and least privilege enforcement can save your business from catastrophic data loss.
Cloud Access Security Brokers (CASB) serve as gatekeepers for your cloud resources. As more businesses accept cloud computing, CASBs ensure your security policies travel with your data, no matter which cloud platform you're using. They provide visibility into cloud application usage while keeping compliance requirements in check.
Data privacy vaults represent a specialized approach to protecting sensitive information. These systems use strong encryption and tokenization while giving developers secure ways to work with data without directly handling it. It's security and privacy by design, centralizing protection controls and making compliance much simpler.
Modern data security solutions typically include automated data findy across all your systems, continuous monitoring of how data moves and who accesses it, enforcement of least privilege controls, real-time threat detection, comprehensive encryption and key management, compliance reporting, data minimization capabilities, seamless integration with existing IT infrastructure, and support for hybrid and multi-cloud environments.
The Impact of AI and Machine Learning in Data Security Solutions
Artificial intelligence isn't science fiction anymore—it's working behind the scenes to make your data security solutions smarter and more effective. These technologies are revolutionizing how we protect digital assets.
Behavioral analytics and anomaly detection powered by AI learn what normal looks like in your organization. When someone accesses files at 3 AM or downloads unusually large amounts of data, AI flags these anomalies faster than any human could. It's like having a security expert who never sleeps and notices everything.
Automated threat response takes protection a step further. Instead of just alerting you to problems, AI can automatically isolate compromised devices, block suspicious network traffic, or revoke questionable access permissions. This hyperautomation shrinks the window of opportunity for attackers from hours to seconds.
Predictive intelligence learns from past attacks and threat patterns to anticipate future vulnerabilities. Rather than constantly playing defense, you can proactively strengthen weak points before attackers find them. It's like having a crystal ball for cybersecurity.
Improved classification accuracy means AI can identify sensitive data with over 95% accuracy, even in messy, unstructured files. This goes far beyond simple keyword searches, using context and machine learning to understand what really needs protection.
As AI becomes more common in business operations, we're seeing the emergence of solutions designed to secure AI itself. These specialized tools help protect AI agents and machine learning models, ensuring that the technologies driving innovation remain secure and trustworthy.
The integration of AI analytics into various security platforms creates a continuous learning cycle that stays ahead of increasingly sophisticated cyber threats. It's an arms race where the good guys are finally getting better weapons.
Choosing and Implementing Your Data Security Arsenal
Selecting the right data security solutions is like choosing the perfect toolbox for your business. You wouldn't use a sledgehammer to fix a delicate watch, and you shouldn't pick security tools without understanding exactly what you're protecting and how your business operates.

The goal isn't just protection—it's building cyber resilience. This means your business can bounce back from attacks, keep running during incidents, and recover quickly when things go wrong. Think of it as building a business that's not just tough, but truly unbreakable.
Business continuity planning forms the backbone of this resilience. Your security solutions should include robust backup systems and disaster recovery strategies that can restore your operations in hours, not days. When a cyber attack hits (and statistics show it's more a matter of "when" than "if"), you need systems that minimize downtime and get you back to serving customers quickly.
Centralized management platforms make your life dramatically easier. Instead of juggling dozens of different security tools with separate dashboards and controls, these platforms give you one clear view of your entire security landscape. Imagine managing thousands of encrypted devices from a single console—that's the kind of efficiency that saves both time and money while reducing the chance of human error.
Your chosen solutions must grow with your dreams. Scalability requirements matter whether you're protecting gigabytes today or planning for petabytes tomorrow. The right data security solutions scale seamlessly as your business expands, adding new users, devices, and data without missing a beat or compromising security.
Budget considerations are always real, but smart security is an investment, not just an expense. We focus on finding solutions with the lowest total cost of ownership, reducing both your operational costs and capital expenditures. The goal is maximum protection that makes financial sense for your specific situation.
Most importantly, your security must align with your business needs. A healthcare practice needs HIPAA compliance, while a retailer focuses on PCI-DSS requirements. If your team works remotely, you need solutions that ensure secure access from anywhere. Your security should support your business goals, never hold them back.
At EnCompass, we've built our reputation in the Cedar Rapids Corridor by understanding that robust data protection isn't just about preventing disasters—it's about enabling confident business growth. When you know your data is secure, you can focus on what really matters: growing your business and serving your customers. We take the IT headaches off your plate so you can concentrate on what you do better than anyone else.
Frequently Asked Questions about Data Security
When we work with businesses across the Cedar Rapids Corridor, certain questions about data security solutions come up again and again. These are the conversations that help organizations move from uncertainty to confidence in their security approach.
What is the first step to improving data security?
Here's the truth that might surprise you: the first step isn't buying the latest security software or hiring more IT staff. It's actually about visibility. You simply cannot protect what you cannot see.
Think of it like trying to secure your home without knowing how many doors and windows you have, or where they're located. That comprehensive assessment to find and classify all your data across every environment—cloud, on-premises, and SaaS applications—becomes your security foundation.
This findy process includes identifying those hidden data repositories that seem to multiply when no one's looking. The good news is that modern data security solutions can achieve over 95% classification accuracy while keeping your sensitive information secure within your own environment. It never has to leave your control during the findy process.
Once you know what data you have and where it lives, everything else becomes possible. Without this visibility, you're essentially playing defense with a blindfold on.
Is encryption alone enough to protect my data?
This question usually comes from organizations that have heard encryption called the "last line of defense" and wonder if they can skip the other lines entirely. While I appreciate the efficiency mindset, encryption alone is like having the world's strongest lock on a door that's standing wide open.
Encryption is absolutely critical and non-negotiable—don't get me wrong. It's that uncrackable vault we talked about earlier. But even the most sophisticated encryption becomes useless if cybercriminals can simply walk around it through weak access controls or if your encryption keys are poorly managed.
A truly effective strategy weaves encryption together with strong access controls, continuous monitoring, and robust key management. Think of it as a coordinated defense system where each component strengthens the others. When these elements work together, you create something much more powerful than any single security measure could provide.
How does cloud security differ from on-premises security?
Cloud security operates on what we call a shared responsibility model, and understanding this division is crucial for avoiding dangerous security gaps.
Here's how it works: your cloud provider handles securing the underlying infrastructure—the physical servers, network hardware, and foundational platform security. That's their job, and they're generally excellent at it. But everything you put in the cloud? That's still your responsibility.
This means you're still accountable for configuring your cloud environments securely, managing user identities and access, encrypting your data, and ensuring compliance with regulations like HIPAA or GDPR. The cloud doesn't automatically make your data secure—it just changes where and how you need to apply your security controls.
Many businesses assume that moving to the cloud means transferring security responsibility entirely. That assumption can create significant vulnerabilities. The key is understanding exactly where your responsibility begins and ensuring your data security solutions work seamlessly across both cloud and on-premises environments.
At EnCompass, we help businesses steer this shared responsibility model, ensuring that your security strategy covers all the bases while taking advantage of the cloud's benefits. After all, our goal is to take these complex IT challenges off your plate so you can focus on growing your business with confidence.
Conclusion
Data security solutions aren't just another line item in your IT budget—they're the difference between a thriving business and one that becomes another cautionary tale in the evening news. We've walked through the maze of modern cybersecurity together, from understanding the complex challenges of hybrid cloud environments to building a fortress-like security strategy that can withstand even the most sophisticated attacks.
The journey we've taken shows us that protecting your data requires more than just installing antivirus software and hoping for the best. It demands a thoughtful approach that starts with knowing exactly what data you have and where it lives, continues with smart access controls that assume nothing and verify everything, and relies on encryption as your ultimate safety net.
What strikes me most about working with businesses across the Cedar Rapids Corridor is how often I hear, "I wish we'd started taking this seriously sooner." The truth is, data security solutions work best when they're implemented as part of your business growth strategy, not as a frantic response to a crisis. Every day you wait is another day your valuable information sits vulnerable to increasingly clever attackers.
The good news? You don't have to figure this out alone. Data security is indeed a continuous journey, not a one-time destination, but it's a journey that becomes much more manageable with the right partner. At EnCompass, we've built our reputation on making complex IT challenges simple for our clients. We understand that your time is better spent growing your business than wrestling with security configurations and compliance requirements.
Your data tells the story of your business—your customers' trust, your financial health, your competitive advantages, and your future plans. That story deserves protection that's as robust and reliable as the business you've worked so hard to build.
Ready to transform your data security from a source of worry into a competitive advantage? Learn more about our IT support services and find how EnCompass can help you sleep better at night, knowing your digital assets are truly secure.


